How to programmatically bypass 2FA

Introduction
There is a chance that one day you’ll be asked to enter a two-factor authentication (2FA) code. There is even a possibility that you’ll be asked to enter a code every time you log in. Such a good area for automation, isn’t it?
My notes are usually dancing around mobile automation, so let’s imagine we have an idea to bypass 2FA on Play Store as part of our automation script.
Action
Indeed the first time we have to log in manually, but instead of a QR code, we’ll use a secret key.
- Navigate to myaccount.google.com/security using the account that will be used in the automation script
-
Click on
2-Step Verificationsection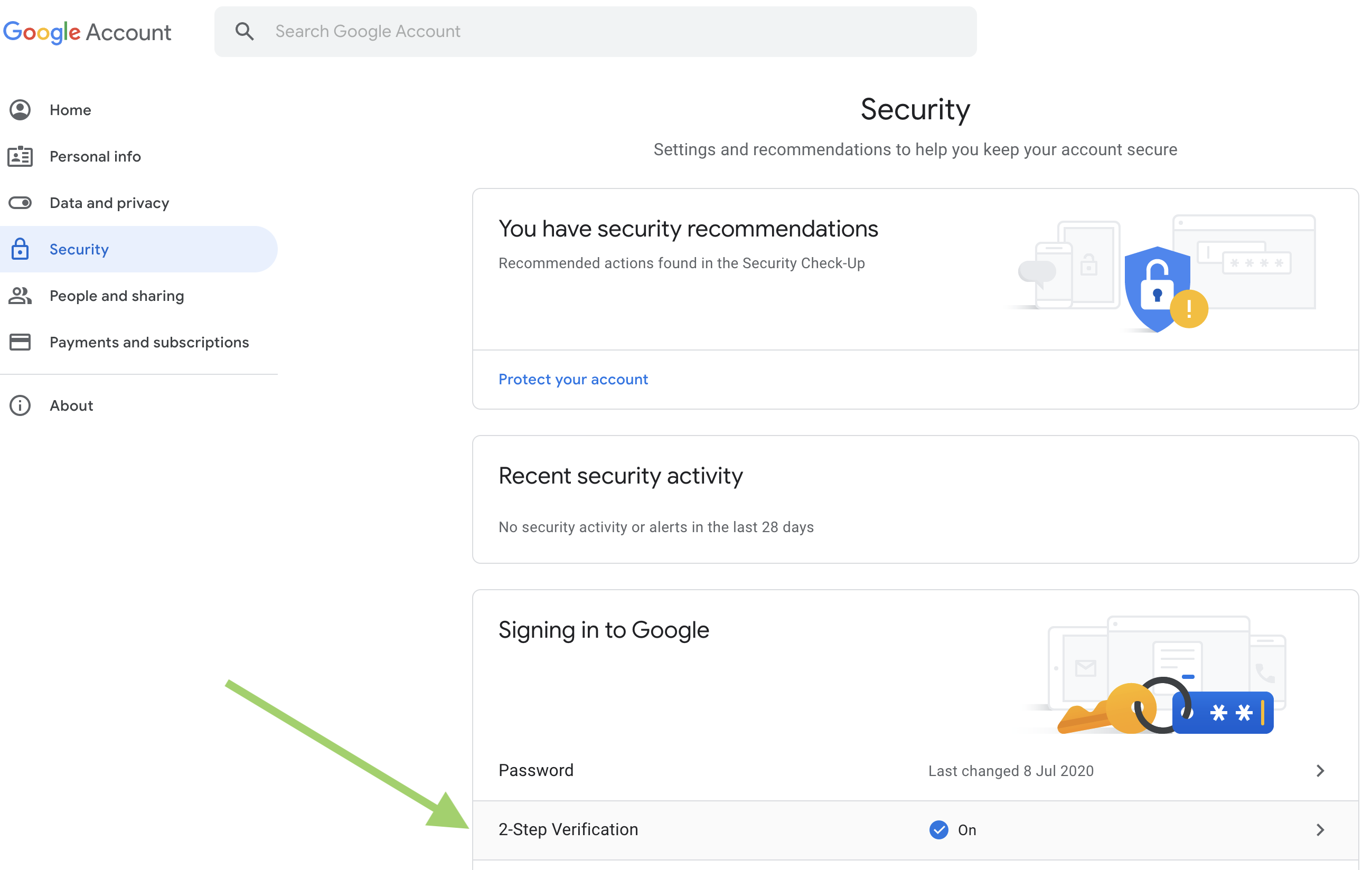
- Provide an email and a password and click on the
Nextbutton -
Click on the
Authenticator Appsection (or on theChange Phonelink in that section if the app was already set up for this account)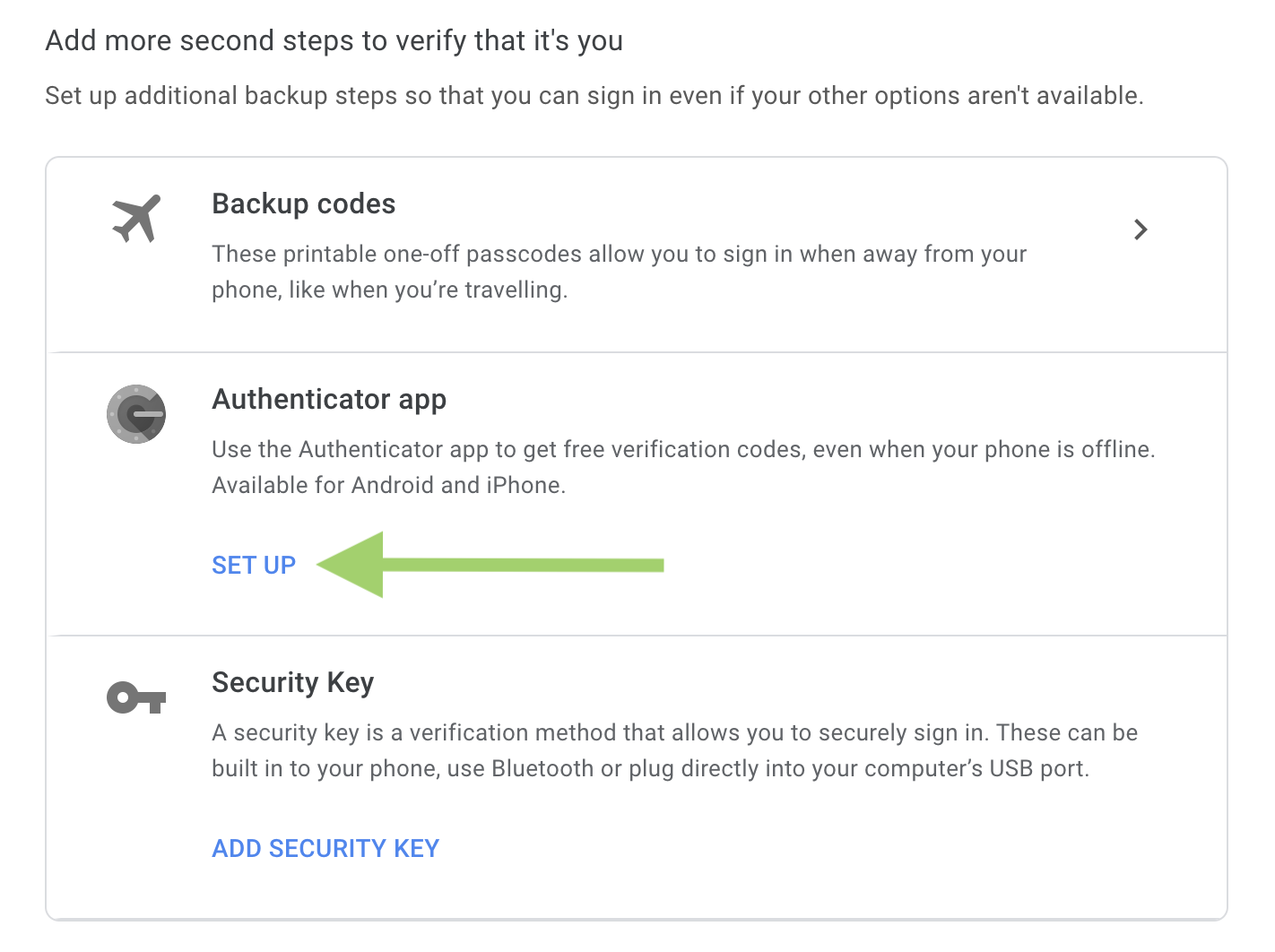
-
Select the
AndroidoriPhoneradio button and click on theNextbutton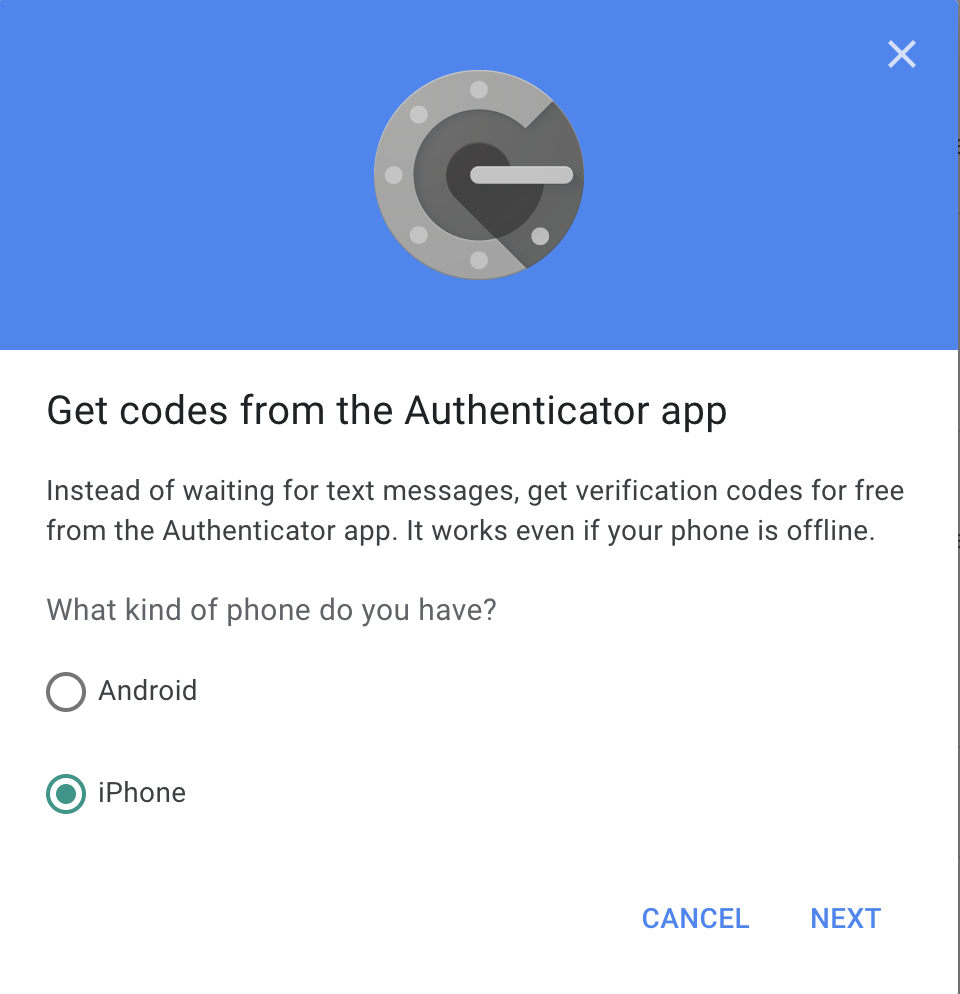
-
Click on the
Can’t Scan Itoption (it will generate thesecret keyfor manual use)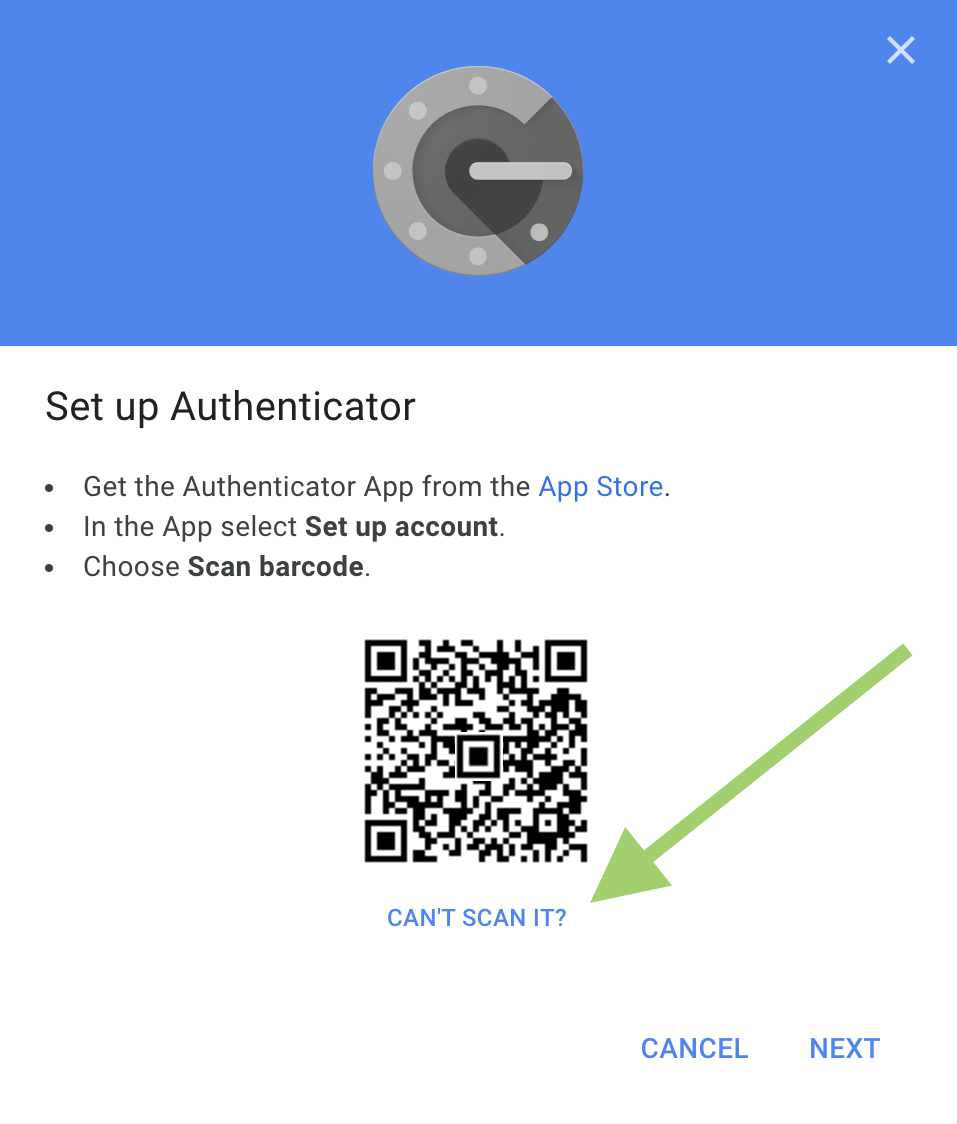
- Open any Authenticator app on your iOS or Android device (e.g.: Duo Mobile)
-
Add a new account in the Authenticator app using the account email and the
secret keyfrom the previous step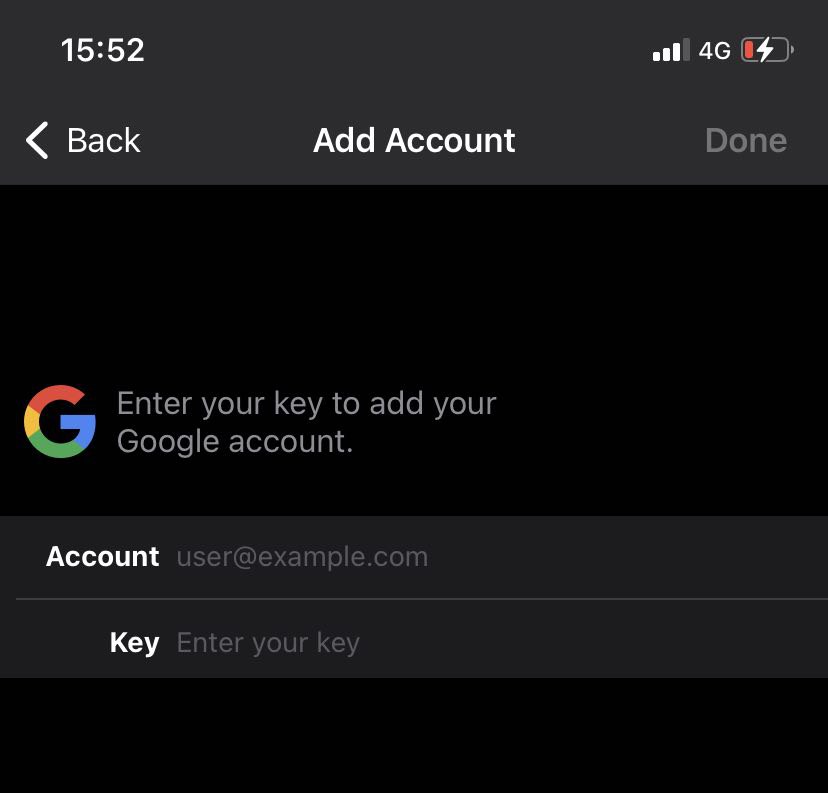
- Return to the browser window and click on the
Nextbutton - Generate a Time-based One-Time Password TOTP using the Authenticator app on your device
-
Jump back on the browser window, enter the TOTP verification code and click on the
Verifybutton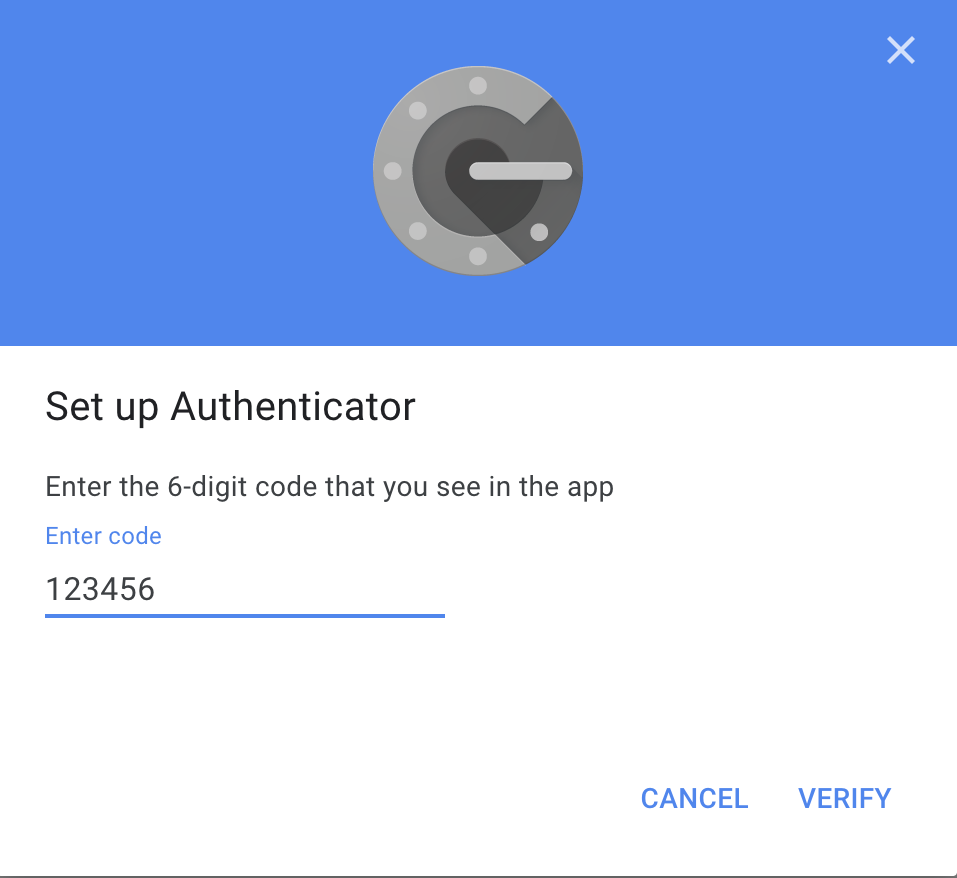
That’s it, we logged in. Now it’s time to automate the process. We’re not going to open the Authenticator app every time we log in, are we?
-
Install OATH Toolkit on your machine:
brew install oath-toolkit -
Generate the TOTP verification code:
oathtool --base32 --totp "${YOUR_SECRET_KEY}"
Cool beans, the output of the last command is the TOTP verification code. Check it out!
Conclusion
Although 2FA is a truly secure thing, but as you might have noticed, it’s also a kind of developer-friendly tool, and to bypass it from the script, automation test or whatever we can simply use oathtool at the moment of logging in. Hope it helps. See ya later (: