iOS apps under the microscope

I once wrote a note about poking around Android apps. The other day I realised I still haven’t done it for iOS. Let’s fix the gap (:
Nice to have
- Hopper Disassembler (free version is enough for now)
- class-dump (binary selection depends on your app)
- passionfruit (for those who like UI) – as it’s kind of archived I’ll update the note right after depreciation of the tool
- objection (for those who adore CLI)
- frida (em, no comments)
- Jailbroken iDevice (whatever, e.g.: checkra1n)
Here we go
As an example I’ll take default Apple’s Calendar app:
com.apple.mobilecal
Binary neighbours
At first we should somehow get hold of decrypted app file (.ipa). To do so we can jump over to another branch where I explained the process in details.
As soon as we got the decrypded .ipa we are able to:
-
Imagine .ipa as archived folder:
mv Calendar.ipa Calendar.zip -
Unzip that folder
unzip Calendar.zip -
Get inside
cd Payload/MobileCal.app/
Being there we can find binary itself (that names «MobileCal» without extension) and figure out what else lives near the binary, e.g.: .json and .plist files.
Strings and pseudocode
As soon as we got the binary file we can dive much deeper – inside the Assembler code via Hopper:
-
Open Hopper Disassembler app
-
Navigate to «File ↝ Open…»
-
Chose the app’s binary file
-
Confirm all default options by tapping on «OK» button
-
Wait for Hopper will analyze binary code
When Hopper has done its awesome work we are able to:
- Consider strings «representation» of our sample app
- Look for methods names
- Enjoy pseudocode of those methods
- Or block diagrams
Classes, methods and variables
Then we could get a list of the classes from the app in a readable format via class-dump:
-
As I mentioned before binary selection depends on your app:
- if your app is written in Objective-C, so grab ObjC binary
- elsif your app is written in Swift, just grab Swift binary
-
Put the binary to
/usr/local/bin/folder -
Dump the app’s binary using class-dump
class-dump-swift Payload/MobileCal.app/MobileCal > dump.txt -
Enjoy classes content by opening dump.txt file
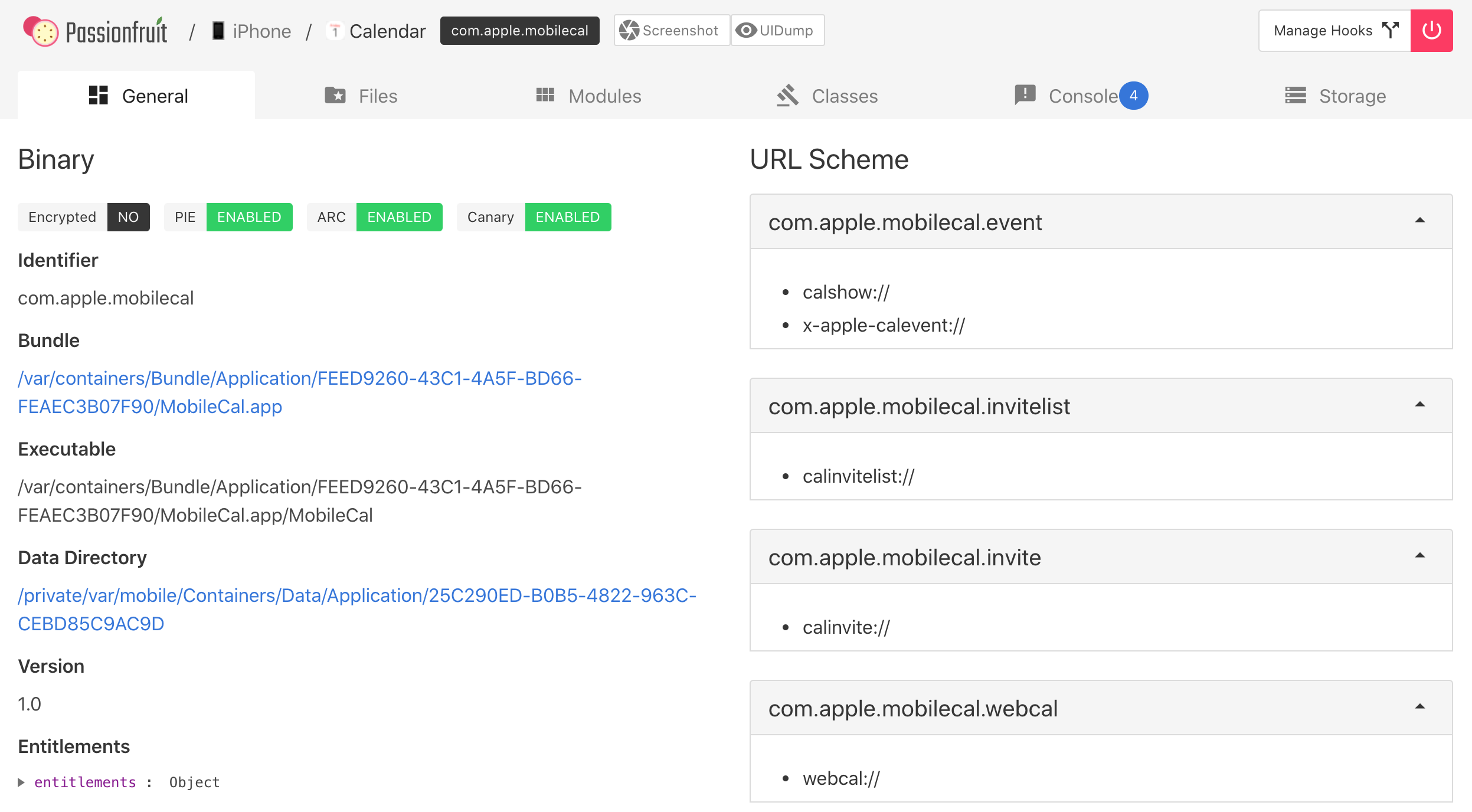
Keychain, local storage, url-schemes and much more
To get this data we could use for example: passionfruit or objection. For most day to day actions, these tools are pretty much the same with only one correction:
- passionfruit is about UI
- objection is about CLI
Just take your choice, but I’ll do a short intro how to get app’s data using both of them:
objection
objection -g "Calendar" explore
| Command | Description |
|---|---|
| ios cookies get | Show app’s cookies |
| ios keychain dump | Show app’s keychain |
| ios nsurlcredentialstorage dump | Show nsurlcredentialstorage data |
| ios ui dump | Show current app’s screen hierarchy |
| ios bundles list_frameworks | Show app’s frameworks list |
| ios plist cat | Show content of chosen plist file |
| sqlite connect | Show content of chosen DB file |
passionfruit
-
Run passionfruit server
passionfruit -
Open its main web page
open http://localhost:31337 -
Chose your device and the app
-
Enjoy handy design with a lot of intuitive features
Widescale static analysis
There were many interesting tools, but let’s come back to old but cozy frida and grep all useful information about the app.
Just run the command and enjoy the output:
frida -U "Calendar" --codeshare interference-security/ios-app-static-analysis
Conclusion
Hope it helped on your way, see ya (:




