Sniffing network traffic on Android ≥7

Introduction
Today I want to write about sniffing network traffic on Android. Let me show you what we had before and what we have after Android Nougat:
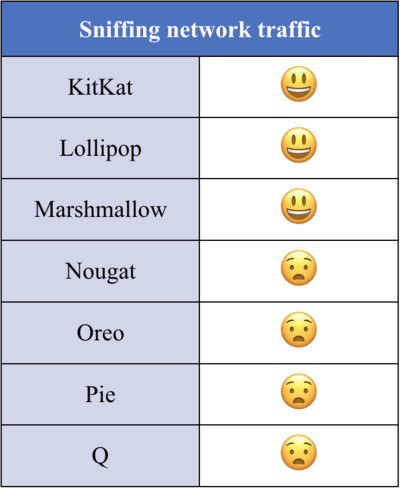
In other words, Google removed the feature to sniff a network traffic out of the box in Android Nougat. Furthermore, it means, that you won’t be able to sniff a network traffic in apps from Play Market. Thereby, we should install network security config manually to resurrect sniffing feature. There are two ways to do it:
- add network_security_config.xml in the source
- inject network_security_config.xml in an .apk file
training/articles/security-config
Addition network_security_config.xml in the source
- default
<?xml version="1.0" encoding="utf-8"?>
<manifest ... >
<application android:networkSecurityConfig="@xml/network_security_config"
... >
...
</application>
</manifest>
- custom
<?xml version="1.0" encoding="utf-8"?>
<network-security-config>
<domain-config>
<domain includeSubdomains="true">example.com</domain>
<trust-anchors>
<certificates src="@raw/my_ca"/>
</trust-anchors>
</domain-config>
</network-security-config>
But there is a high probability, that Google may reject apps have network_security_config.xml, because it’s a «care» about peace, rock ‘n’ roll and safety.
Injection network_security_config.xml in an .apk file
Here we are able to build a release .apk, duplicate it and make a network_security_config.xml injection. So, let’s start:
- Build an .apk
-
Clone the repo:
git clone https://github.com/levyitay/AddSecurityExceptionAndroid.git -
Run a script from the repo:
./addSecurityExceptions.sh yourApp.apk- the script unpacks your .apk via apktool
- injects network_security_config.xml into AndroidManifest.xml
- signs and repacks your .apk
- Your app is ready for test, install it and enjoy the sniffing
Conclusion
Hope it was interesting or at least a bit useful (:
Thanks for the reading and see you!